7 Managed Cloud Security Services Providers Review for SMBs: Top MSSPs Compared
Almost 48 percent of U.S. small and midsize businesses have suffered a cyber-attack, and 52 percent still rely on untrained staff to fight back, according to an ITPro report. According to ACSMI, each breach drains an average of $3.3 million in downtime, fines, and brand damage.
This guide flips those odds. We compare seven cloud-first security partners—spotlighting where they shine, where they stumble, and which one suits your business. You can also lean on an advanced solutions provider to bundle the right mix of tools and talent.
How we chose these providers
You deserve clear, transparent criteria, not a popularity contest.
We started with Channel Insider’s scoring model, which weighs core features, cost, security operations, ease of roll-out, integration, and support, then adjusted the formula for cloud-first realities.
Security breadth and cloud coverage top the list. If a provider can’t monitor AWS, Azure, and SaaS tools alongside your laptops, it’s out.
Pricing clarity comes next. Fixed per-device plans or published entry tiers earn points because they let you budget without a “call for quote” surprise.
Compliance strength ranks third. From PCI checklists to FTC Safeguards reports, we looked for vendors that give you audit-ready evidence, not homework.
Speed and quality of response follow. A 24-hour ticket won’t cut it when ransomware can encrypt files in minutes, so we favored firms with minute-level SLAs and named advisers.
Finally, we scanned customer reviews for real-world friction such as onboarding hiccups, hidden fees, and standout support.
Seven providers met all criteria, and you’ll meet them next.
TD SYNNEX Advanced Solutions
Built around its TD SYNNEX Advanced Solutions ecosystem, which streamlines modern infrastructure and high-growth technology projects, the company isn’t a traditional MSSP. It acts as a matchmaker, pairing you with vetted security vendors, cloud infrastructure, and on-call expertise, all under one roof.
You begin with a consultative workshop. Architects map the risks in your workloads, then recommend a pre-built bundle or design something bespoke. With a catalog of over 100 ready-to-deploy packages, you skip the months of vendor chasing most SMBs face.
Choice is the advantage. Want an MDR engine from Arctic Wolf, a cloud firewall from Palo Alto Networks, and compliance reporting from Vanta? TD SYNNEX stitches the pieces together, handles licensing, and connects you to a certified partner who manages daily security.
The breadth of options can overwhelm if you expect one invoice and one portal. Results hinge on the partner you select, so verify their track record before signing.
Best for growing businesses that need end-to-end cloud security without locking into a single vendor stack.
Arctic Wolf
Picture a 24 × 7 security operations center that learns your environment, chases threats, and hands you a plain-language action plan before lunch. That is Arctic Wolf.
The Concierge Security Team pairs automated detection with named analysts who know your network by heart. You get one phone number, one shared Slack channel, and a response time measured in minutes, not hours. For an SMB without in-house defenders, that level of guidance feels almost unfair—in the best way.
Deployment stays simple. Drop a lightweight sensor on your firewall, connect cloud accounts with API keys, and the platform starts ranking risks with color-coded clarity. No forklifts, no surprise hardware costs.
Pricing is upfront: a flat per-asset subscription that scales as you add users or servers. Smaller shops may find the entry tier steep, and companies with a seasoned SOC could view constant guidance as overkill.
Choose Arctic Wolf when you want an outsourced security team that still feels in-house. It is especially helpful for regional businesses facing their first compliance audit or ransomware scare.
Alert Logic
If your workloads run in AWS, Azure, or a hybrid mix, Alert Logic is purpose-built for you.
The service is fully SaaS. Connect cloud accounts, turn on log collection, and the threat analytics engine starts flagging misconfigurations, credential abuse, and workload attacks in hours rather than weeks.
Round-the-clock analysts sit behind the dashboard. They investigate every critical alert and send step-by-step remediation guidance to your inbox or ticketing system. Need evidence for an auditor? One click exports PCI- or HIPAA-ready reports.
Alert Logic earns points for fast onboarding and flexible pricing. You can start with a handful of cloud assets and expand as new regions or containers launch. Because everything runs in the cloud, there is no appliance tax and no surprise maintenance bill.
Trade-offs matter. On-prem visibility still leans on virtual sensors instead of deep-packet appliances, and niche forensic services often require an add-on. Branding can also confuse newcomers since Alert Logic now operates under the Fortra umbrella.
Choose Alert Logic when cloud risk keeps you up at night and you want a security partner fluent in AWS, Azure, and container security.
eSentire
Certain threats slip past rule-based detection. eSentire hunts for those ghosts 24 hours a day.
The Atlas XDR platform ingests logs, network flows, and endpoint telemetry, then flags anomalies that machine learning cannot dismiss. Human threat hunters step in, isolate the root cause, and, on average, contain lateral movement in under 20 minutes.
That speed matters for regulated firms. Financial advisors, healthcare startups, and legal practices choose eSentire because analysts back each alert with forensics-grade evidence you can hand straight to auditors. Need a virtual CISO to refine policies or brief the board? It comes with the service.
Expect a premium price. eSentire’s white-glove investigations cost more than “monitor and email” MSSPs. You will also complete a structured onboarding program that requests log sources, asset inventories, and security objectives. The homework pays off in tailored detections but can surprise teams looking for instant setup.
Pick eSentire when compliance is non-negotiable and you cannot risk even one breach headline with your name on it.
Expel
Many security vendors hide their playbook. Expel hands you the whole chalkboard.
Open your dashboard and you can watch analysts triage alerts in real time, review their reasoning, and even comment back. That transparency builds trust quickly, which explains why cloud-native startups flock to the service.
Integrations are API-first. Point Expel at Microsoft 365, AWS CloudTrail, Google Workspace, SentinelOne, and more than 70 other sources, and the system stitches context without extra agents. You keep the tools you already own; Expel just thinks for them.
When trouble strikes, analysts act or guide—your choice. Give them full authority and they isolate hosts, revoke tokens, and close tickets automatically. Prefer a co-managed approach? They send a fix script and remain on the call until you confirm success.
The model is subscription-based and asset-count driven, so costs rise as you grow. Small firms may also need to deploy an EDR platform first, since Expel expects data to flow from somewhere.
Choose Expel if you crave SOC expertise yet dislike black boxes. You’ll learn as you secure, and that combination suits fast-moving teams.
Sophos managed security
Sophos earned its reputation in endpoint and firewall tools, then bundled them into a managed detection and response service built for SMBs.
Everything feeds into Sophos Central. One cloud console shows malware events on laptops, blocked phishing emails, and risky AWS settings side by side. The MDR team watches the same screen. When something spikes, they isolate the device or user account and send a plain-language summary so you know exactly what happened.
Because Sophos owns the entire stack—firewall, endpoint, email, cloud posture—you skip the finger-pointing that slows multi-vendor setups. Updates arrive automatically, and the interface feels consistent whether you protect ten seats or ten thousand.
The trade-off: the service works best if you run Sophos gear across the board. Mixing third-party firewalls or EDRs is possible but loses some of the single-pane simplicity and can increase costs.
Choose Sophos when you want one vendor, one bill, and one phone number for all things security. It is a straightforward option that still delivers enterprise-level protection.
Trustwave
Swipe a credit card, store patient charts, or run point-of-sale terminals, and compliance pressure follows. Trustwave was built for that reality.
The SpiderLabs team mixes managed detection with penetration testing and digital forensics, helping you tighten defenses and document proof. The Trustwave Fusion portal bundles more than 12 tools, including SIEM, vulnerability scanning, web application firewall, and managed email security, into one dashboard you can filter by PCI, HIPAA, or GDPR controls.
Retailers appreciate the extras: remote POS monitoring, mobile device security, and web malware scans that flag a hacked storefront before Google blocks it. Each module connects to the same 24 × 7 SOC, so alerts stay consistent no matter where trouble starts.
Pricing is custom and can rise as you activate additional modules. Global support also varies; confirm local SLAs and language coverage before signing.
Choose Trustwave when auditors keep sending questionnaires and you want one partner that can both secure and certify your environment.
Comparison at a glance
You just met the seven contenders. Now compare them side by side to spot strengths quickly.
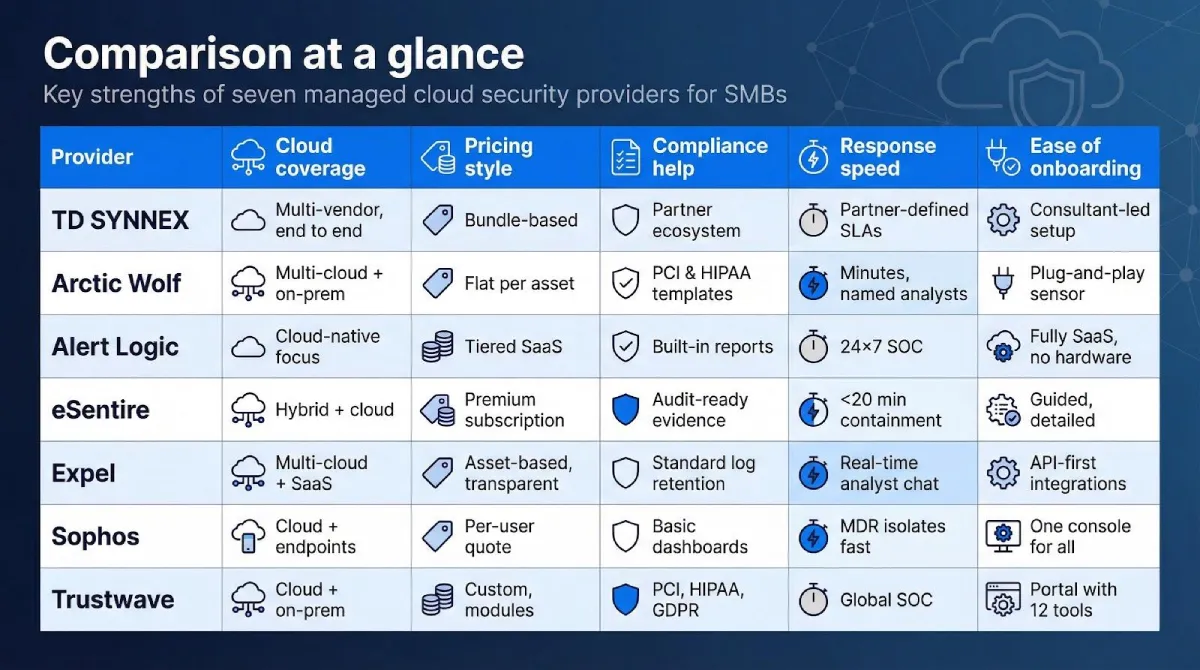
| Provider | Cloud coverage | Pricing style | Compliance help | Response speed | Ease of onboarding |
| TD SYNNEX | Multi-vendor, end to end | Varies by bundle | Strong via partner ecosystem | Partner-defined SLAs | Consultant-led setup |
| Arctic Wolf | Multi-cloud + on-prem | Flat per asset | PCI and HIPAA templates | Named analysts respond in minutes | Plug-and-play sensor |
| Alert Logic | Cloud-native focus | Tiered, SaaS | Built-in reports | 24 × 7 SOC | Fully SaaS, no hardware |
| eSentire | Hybrid + cloud | Premium subscription | Audit-ready evidence | Containment in under 20 minutes | Guided but detailed |
| Expel | Multi-cloud + SaaS | Asset-based, transparent | Standard log retention | Real-time analyst chat | API integrations |
| Sophos | Cloud + endpoints | Quote-based per user | Basic dashboards | MDR team isolates threats fast | One console for all |
| Trustwave | Cloud + on-prem | Custom, module driven | PCI, HIPAA, GDPR suites | Global SOC, varies by region | Portal with 12 tools |
Use the table to narrow your options. Circle the two or three providers that match your priorities, then return to their snapshots for deeper evaluation.
Which provider fits your SMB?
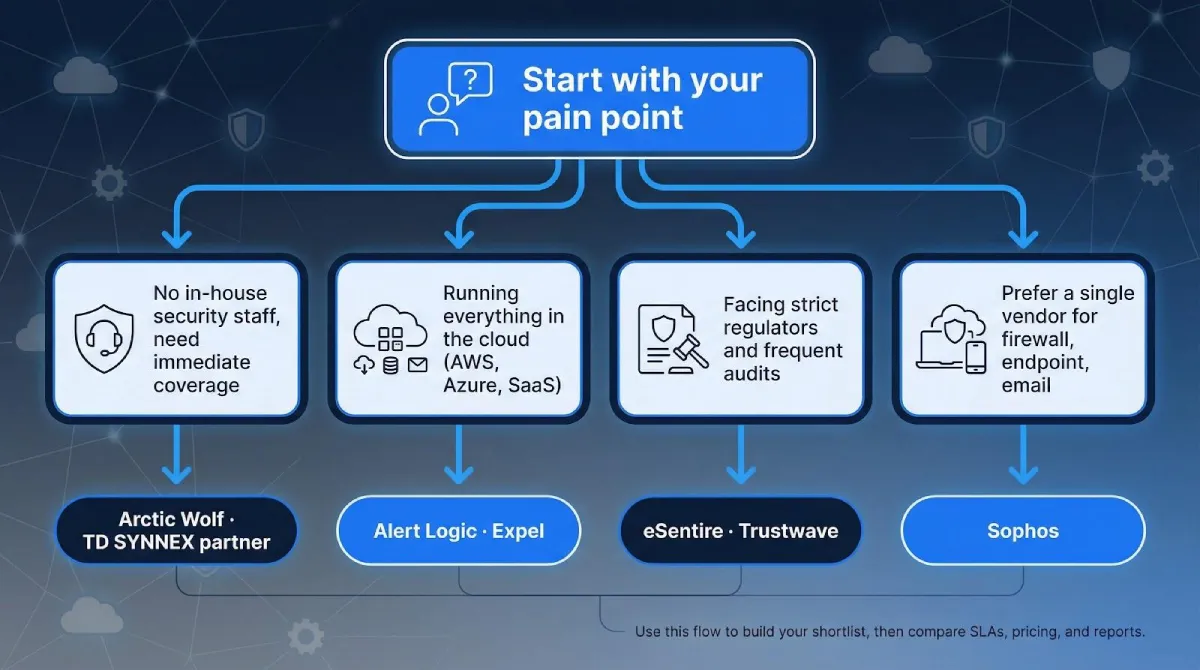
Start with your pain point, not the provider’s pitch.
If you lack in-house security staff and need immediate coverage, Arctic Wolf or a TD SYNNEX partner can spin up a staffed SOC overnight.
Running everything in the cloud? Alert Logic and Expel connect to AWS, Azure, and SaaS APIs within a few hours and begin hunting threats the same day.
Facing strict regulators? eSentire and Trustwave weave audit evidence into daily operations, delivering the files your accountant and insurer expect.
Prefer a single vendor for firewall, endpoint, and email security? Sophos keeps every alert in one console and on one invoice.
Use these realities to narrow your list, book demos, and ask three blunt questions:
- How fast will you contain a live ransomware incident?
- What will my first year cost, including onboarding?
- Show me a sample compliance report I can hand to auditors.
Their answers reveal the right match faster than any glossy brochure.
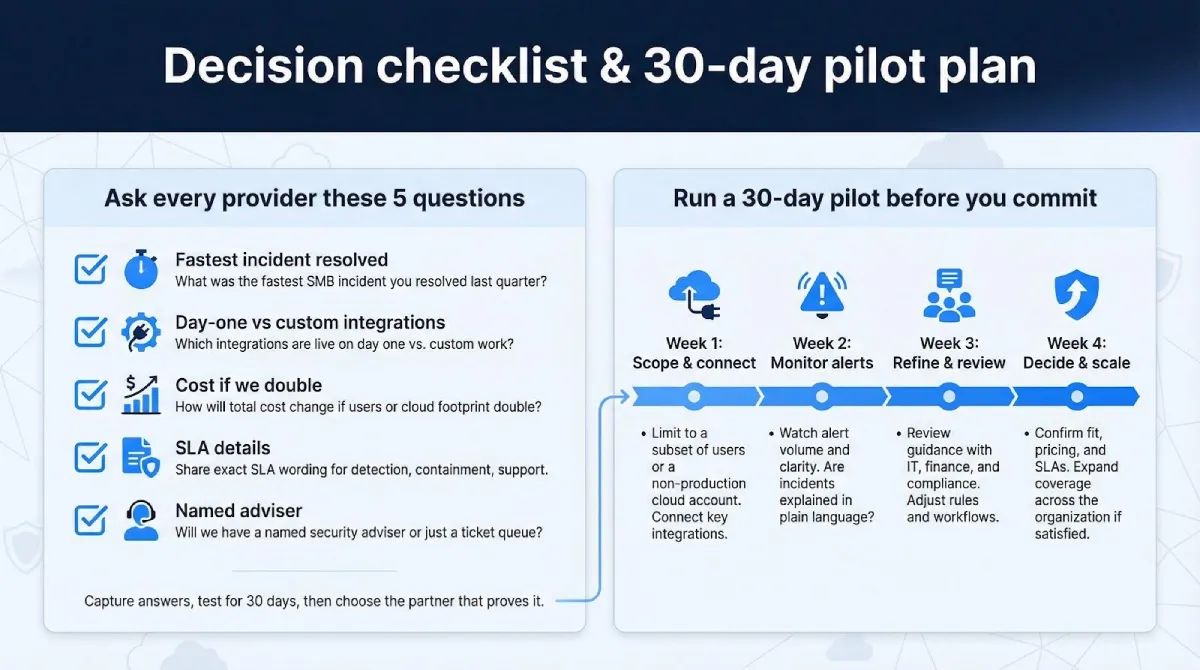
Decision checklist and next steps
You have a shortlist and a sense of fit. Now confirm it.
Ask each provider the same five questions to keep comparisons fair:
- What was the fastest incident you resolved for an SMB last quarter, start to finish?
- Which integrations will be live on day one, and which will require custom work?
- How will total cost change if my user count or cloud footprint doubles next year?
- Share the exact SLA wording for detection, containment, and customer support.
- Will I have a named security adviser or just a ticket queue?
Capture the answers, then invite your finance lead and compliance officer to the demo recap. Their feedback surfaces early, not after the contract is signed.
Next, run a 30-day pilot. Monitor a subset of users or a non-production cloud account. If alerts arrive quickly, guidance is clear, and pricing matches your budget, expand protection across the organization.
Choosing the right partner today sets you up for safer growth tomorrow.


Leave a Reply